

Excellent topic — Zero Trust Architecture (ZTA) in Legacy Systems is where cutting-edge security theory hits real-world IT headaches. This is a super relevant issue for governments, big corporations, and anyone stuck with old tech stacks that weren’t built with modern cyber threats in mind.
Here’s a full breakdown you can use for a paper, talk, or project:
Implementing Zero Trust Architecture in Legacy Systems: Challenges, Strategies, and Opportunities
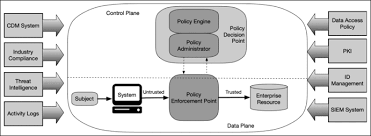
Zero Trust Architecture (ZTA) is the modern cybersecurity paradigm that assumes no device, user, or system is inherently trusted — even inside the network perimeter. But applying ZTA to legacy systems, which often lack modern security features and were never designed for this model, poses serious challenges. This topic explores how organizations can retrofit older systems for Zero Trust and what strategies can bridge the gap between theory and practical implementation.
“Never trust, always verify” principle.
Key components:
Identity & Access Management (IAM)
Microsegmentation
Multi-Factor Authentication (MFA)
Continuous monitoring and analytics
Least privilege access
Older software/hardware still in use due to:
Cost of replacement
Mission-critical dependencies
Lack of vendor support
Regulatory lock-in (e.g., healthcare, government)
Examples: Mainframes, Windows XP-based control panels, COBOL systems in banks, old SCADA systems in manufacturing
No native support for MFA, encryption, or logging
Poor network visibility
Hardcoded credentials or lack of IAM integration
Inability to patch or upgrade
Flat network architectures
Network Segmentation & Microsegmentation
Isolate legacy systems using VLANs or software-defined perimeters.
Wrap in Security Proxies or Gateways
Use reverse proxies or API gateways to enforce ZTA policies externally.
Identity Federation
Implement identity brokering to apply modern IAM rules around legacy systems.
Zero Trust “Overlay” Solutions
Tools like Zscaler, Illumio, or Banyan Security can add ZTA-style controls without rewriting legacy software.
Monitoring & Behavioral Analytics
Use anomaly detection to monitor system interactions even if internal logging is weak.
U.S. Federal Agencies: Under Executive Order 14028, many agencies must modernize with ZTA but are heavily reliant on legacy systems.
Banks: COBOL-based systems wrapped with APIs and IAM tools for secure access.
Healthcare: Old medical devices segmented and accessed via secure jump hosts.
Identity Providers (Okta, Azure AD)
To manage access externally even if the system doesn’t support SSO.
Privileged Access Management (PAM)
Tools like CyberArk and BeyondTrust enforce least privilege.
Endpoint Detection & Response (EDR)
Monitor legacy endpoints for unusual behavior.
Network Access Control (NAC)
Tools like Cisco ISE control who gets to access the network and how.
Cost: Retrofitting ZTA can be expensive and time-consuming.
Downtime risks: Making changes to fragile systems may cause failures.
Compliance gaps: Legacy systems often fail modern compliance tests.
Cultural resistance: Teams may resist changes to systems “that have always worked.”
Legacy systems won't disappear overnight — hybrid ZTA will dominate for the next decade.
AI-driven ZTA solutions may help detect trust violations without deep system integration.
Governments and large orgs are pushing hard for ZTA adoption — zero trust mandates are coming.
NIST SP 800-207: Zero Trust Architecture
Microsoft’s Zero Trust Deployment Guide
Forrester Research: Zero Trust eXtended Ecosystem
Cybersecurity & Infrastructure Security Agency (CISA): ZTA Maturity Model
Case Study: "Zero Trust in a Hospital with Legacy Medical Devices"
Comparative Analysis: "Microsegmentation vs Network Isolation for Legacy Protection"
Simulation: Design a Zero Trust overlay for a fictional legacy SCADA environment
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com