


Digital Identity is the digital representation of a person, organization, or device. It includes:
Login credentials
Biometrics
Personal attributes (name, age, nationality)
Behavioral data
Device IDs and credentials
These identities are used to authenticate, authorize, and verify users across systems.
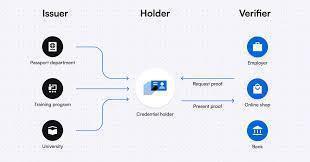
A DID is a self-owned, cryptographically secure digital identifier that allows individuals or entities to prove who they are without relying on centralized authorities.
User control over identity
No central registry (e.g., no dependency on Google, Facebook, or governments)
Blockchain or DLT-based for immutable, verifiable records
Interoperable standards (W3C DID spec)
Cybersecurity ensures the confidentiality, integrity, availability, and authenticity of identity systems.
| Cybersecurity Aspect | Role in Digital ID & DID |
|---|---|
| Encryption & Key Management | Protects private keys tied to a DID |
| Authentication Protocols | Secure login mechanisms (MFA, biometrics, passkeys) |
| Access Control | Limits who/what can interact with identity data |
| Zero Trust Architecture | Verifies every identity, every time |
| Secure Hardware (TPM/HSM) | Protects private keys on user devices |
| Anomaly Detection | Identifies identity fraud or misuse |
| Resilience to Sybil Attacks | Crucial for decentralized environments |
Public-Key Cryptography
DIDs are tied to a public-private key pair
Only the key holder can prove ownership
Verifiable Credentials (VCs)
Digitally signed documents (e.g., driver's license, diploma)
Verifiers can validate authenticity without contacting issuers
Selective Disclosure
Users reveal only the data needed for a transaction (e.g., age verification without giving your birthdate)
Revocation Mechanisms
DIDs or credentials can be revoked securely and traceably
| Challenge | Description |
|---|---|
| Key Loss/Compromise | Losing private keys = losing identity |
| Phishing & Social Engineering | Attackers may trick users into signing malicious transactions |
| Scalability of Trust | Verifying credentials at scale without bottlenecks |
| Interoperability Issues | Standards are still evolving |
| Malicious Credential Issuers | Verifiable doesn’t always mean truthful |
Microsoft ION (built on Bitcoin) – Decentralized identity layer using Sidetree
Sovrin Network – A public-permissioned ledger for self-sovereign identity
EU eIDAS 2.0 – Working toward European Digital Identity Wallets with DIDs and VCs
Hyperledger Indy – Open source infrastructure for decentralized identity
Web3 & Identity – Wallets as digital passports
Privacy-Preserving Authentication – Zero-knowledge proofs (ZKPs) in identity verification
Post-Quantum Cryptography – Future-proofing DID systems against quantum threats
AI & Identity Fraud Detection – Smart monitoring of DID usage across platforms
Decentralized Access Management – Fine-grained, user-controlled permissions in dApps
| Without strong cybersecurity, decentralized identity is a liability — not an asset. |
|---|
| Ensuring trust, privacy, and control in decentralized identity ecosystems demands robust, adaptive, and forward-looking security models. |
Would you like:
📘 A policy paper version of this?
🧑💻 A technical breakdown for implementation teams?
🖼️ A visual infographic or architectural diagram?
Also happy to dive deeper into use cases like healthcare, education, finance, or Web3 identity standards like DIDComm or VC-JWTs if you’re going specific!
#trending #latest

Explore the Duolingo English Test for Indian Students Abroad... Read More.

Simple Steps to Get Your Canada Student Visa in 2025... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com