

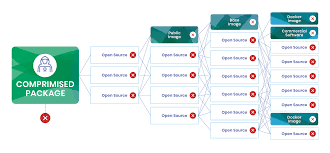
A software supply chain consists of all components — code, libraries, frameworks, dependencies, tools, and infrastructure — used to develop, build, and distribute software.
Source code (internal + open source)
Package managers (npm, PyPI, Maven, etc.)
CI/CD pipelines (GitHub Actions, Jenkins)
Build tools and containers (Docker, Kubernetes)
Repositories (GitHub, GitLab, Bitbucket)
Infrastructure-as-Code (Terraform, Helm, etc.)
Open source components are everywhere, but they come with:
Unknown authorship or limited vetting
Outdated or abandoned packages
Weak/default security settings
Indirect dependencies (the "dependency of a dependency")
Widespread reuse, making a single compromise catastrophic
🧨 Attackers target the supply chain because:
"Why hack a company when you can hack the open-source project they all use?"
| Incident | Description |
|---|---|
| SolarWinds (2020) | Compromised build system injected backdoor into Orion software |
| Log4Shell (2021) | Critical zero-day in Log4j, used in countless Java projects |
| Event-Stream/NPM (2018) | Maintainer handed over package to attacker who added malicious code |
| Colors.js/Faker.js (2022) | Maintainer sabotaged own packages causing system crashes |
| XZ Utils Backdoor (2024) | Stealth backdoor inserted into core Linux tool; nearly shipped in Debian |
Deep chains of dependencies = hidden vulnerabilities
Transitive dependencies often unmonitored
Maintainers may be overworked, underfunded, or replaced by bad actors
Secrets accidentally committed to public repos or packages
Attacks targeting automation scripts, build servers, or containers
Fake packages with names like reqeust or numpyy to trick developers
Use SBOMs (Software Bill of Materials) – Know what’s in your code
Pin exact dependency versions – Avoid unexpected updates
Audit dependencies regularly – Tools: Snyk, Dependabot, OSS Review Toolkit
Adopt signed packages & reproducible builds – Prevent tampering
Isolate and monitor CI/CD environments – Least privilege, role-based access
Use tools like sigstore or cosign – For cryptographic signing and verification
Rotate and protect credentials – Use 2FA, token scanning
Set up project ownership governance – Don’t just “hand off” packages
Use GitHub security advisories & alerts
Adopt tools like OpenSSF Scorecards to measure project health
| Organization/Initiative | Purpose |
|---|---|
| OpenSSF (Open Source Security Foundation) | Best practices, scorecards, funding for OSS sec |
| SLSA (Supply Chain Levels for Software Artifacts) | Framework for secure build systems |
| SPDX & CycloneDX | Standards for Software Bill of Materials (SBOMs) |
| sigstore | Easy code signing for containers, artifacts |
| CISA’s SBOM Initiative | U.S. government push for SBOM adoption |
AI-generated code dependencies – May include insecure patterns or toxic licenses
Runtime monitoring for OSS components – Behavior analysis at deployment
Automated exploit discovery in CI pipelines
Federated attestation – Verifying code origins across supply chains
| Takeaway | Description |
|---|---|
| OSS is essential but risky | Widespread use = widespread exposure |
| Supply chain is now the primary attack vector | Weakest link can bring down the strongest system |
| Cyber hygiene and tooling are non-optional | Regular auditing, SBOMs, signed builds = baseline now |
I can help you:
Build a custom SBOM analysis strategy
Create a DevSecOps supply chain policy
Analyze your dependency tree for weak spots
Draft a whitepaper or slide deck on OSS supply chain security
Let me know what format or direction you're targeting (e.g., CISO briefing, hands-on engineering checklist, compliance-focused doc, etc.) and I’ll tailor it!
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com