

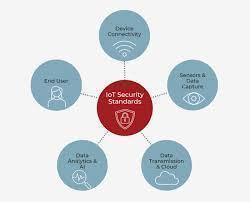
Internet of Things (IoT) devices are now embedded in:
Homes (smart speakers, thermostats)
Healthcare (remote monitors, pacemakers)
Cities (traffic systems, surveillance)
Industry (manufacturing, logistics)
Critical Infrastructure (power grids, water systems)
👉 These devices are often under-secured but highly interconnected, making them attractive targets for cyberattacks.
Botnets (e.g., Mirai) that turn IoT devices into DDoS armies.
Surveillance & Privacy Breaches – Exploited webcams, smart TVs.
Infrastructure Sabotage – Manipulating industrial IoT to cause real-world damage.
Supply Chain Attacks – Infected firmware or malicious updates.
United States
IoT Cybersecurity Improvement Act (2020) – Applies to federal procurement; requires NIST standards.
United Kingdom
Product Security and Telecommunications Infrastructure (PSTI) Bill (2023) – Mandates unique passwords, vulnerability reporting, and support timelines.
European Union
Cyber Resilience Act (CRA) – Expands to cover consumer and business IoT with strict manufacturer responsibilities.
China
Strict domestic standards, emphasizing supply chain control and data sovereignty.
ETSI EN 303 645 – Leading international baseline for consumer IoT security (passwords, updates, secure comms).
ISO/IEC 27400 – General security framework for IoT.
ITU-T (United Nations’ telecom arm) – Recommends global cybersecurity practices.
| Requirement | Why It Matters |
|---|---|
| No default passwords | Prevents mass exploitation |
| Regular software updates | Closes vulnerabilities post-deployment |
| Secure data transmission | Prevents eavesdropping or tampering |
| User transparency | Alerts users to breaches or updates |
| Vulnerability disclosure policies | Encourages ethical hacking and fixes |
Fragmentation – Varying rules by country complicate manufacturing and compliance.
Low-cost Devices – Manufacturers cut corners on security to reduce costs.
Legacy Systems – Billions of insecure, unpatchable devices are already in use.
Accountability – Determining liability in multinational IoT systems is tricky.
Global Baseline Standards – Push toward harmonized, mandatory security standards (think: CE marking for cybersecurity).
Certification & Labeling – Like “energy ratings” but for cyber hygiene.
AI-Driven Security – Smart threat detection on-device.
Built-in Compliance Chips – Secure hardware modules (e.g., TPMs) in even basic devices.
Digital Sovereignty – Nations want control over data generated by IoT.
Cyber Diplomacy – Security standards are becoming tools in trade wars and diplomacy.
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com