

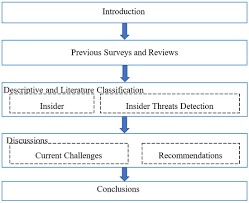
As cyber threats evolve, traditional security approaches that rely on perimeter defense and credential-based access are no longer enough. One of the most elusive and damaging risks comes from within — insider threats. Leveraging behavioral biometrics offers a next-gen, adaptive way to detect and mitigate these threats in real time.
Insider Threats involve current or former employees, contractors, or partners who misuse access privileges.
They fall into three categories:
| Type | Description |
|---|---|
| Malicious | Intentional harm (espionage, theft, sabotage) |
| Negligent | Unintended actions (e.g. weak passwords, phishing) |
| Compromised | External actors using hijacked internal accounts |
Behavioral biometrics analyze patterns of human interaction with digital systems, creating unique behavioral profiles.
Keystroke dynamics: typing speed, cadence, pressure
Mouse movements: paths, acceleration, click behavior
Touchscreen usage: swipe direction, touch pressure
System usage habits: login times, document access sequences
Navigation patterns: how users browse or query data
These are non-invasive, continuous, and difficult to spoof.
Behavioral Profiling
AI/ML models build a digital behavioral signature for each user.
Continuous Monitoring
Activity is tracked passively in real-time across sessions.
Anomaly Detection
Deviations from the user’s norm or from role-based baselines are flagged.
Response & Mitigation
Trigger alerts, challenge with MFA, restrict access, or lock account.
| Technology | Function |
|---|---|
| Machine Learning | Builds behavior models and detects anomalies |
| Deep Learning | Increases accuracy and context sensitivity |
| Natural Language Processing (NLP) | For analyzing text-based behaviors (e.g., chats, commands) |
| Behavioral Analytics | Correlates actions with risk scoring |
| Behavior Change | Possible Risk |
|---|---|
| Login at unusual times | Credential sharing or compromised access |
| Fast or erratic mouse usage | Non-human or scripted behavior |
| Unusual file access patterns | Data theft or policy violation |
| Typing style significantly changes | Credential compromise |
| High volume of downloads | Exfiltration attempt |
Banking/Finance: Detecting rogue traders or data leaks
Healthcare: Preventing unauthorized patient data access
Government/Military: Insider espionage detection
Corporate IT: Preventing IP theft by disgruntled employees
| Challenge | Mitigation Strategy |
|---|---|
| False Positives | Use layered detection + contextual risk |
| Privacy Concerns | Transparent policies + anonymized data |
| Integration Complexity | API-ready platforms, SIEM/SOC integration |
| Behavioral Drift | Regular model updates via adaptive ML |
Integration with Zero Trust: Real-time context for access decisions
Federated Behavioral Models: Preserving privacy while learning across users
Biometrics-as-a-Service (BaaS): Scalable cloud-based behavior detection
Behavior-Based MFA: Invisible step-up authentication
Behavioral biometrics enable continuous, context-aware security by verifying who you are by how you behave. As insider threats grow more sophisticated, integrating these systems into your cybersecurity strategy is no longer optional — it's essential.
Would you like this turned into a:
Slide deck?
PDF whitepaper?
Executive one-pager?
Technical implementation guide?
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com