

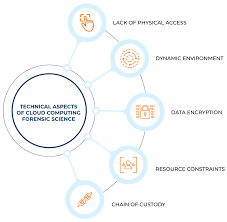
Digital forensics in cloud-native environments presents unique challenges and opportunities for security professionals. With the increasing adoption of cloud technologies, especially in cloud-native architectures (like containers, microservices, and serverless computing), the process of investigating cyber incidents, securing evidence, and conducting forensic analysis has evolved. Cloud-native environments differ significantly from traditional on-premise systems, requiring new approaches to digital forensics. This topic is crucial as organizations need to ensure data integrity, security, and compliance while leveraging cloud technologies.
Let’s break down the key aspects of digital forensics in cloud-native environments.
Cloud-native environments refer to applications and services designed to operate in the cloud, leveraging cloud platforms' scalability, flexibility, and availability. These environments typically include:
Microservices: Small, independent services that communicate over the network.
Containers: Lightweight, portable units of software that encapsulate microservices, typically orchestrated by Kubernetes.
Serverless computing: A model where the cloud provider manages the infrastructure and resources, executing functions or applications as needed.
Unlike traditional environments, cloud-native architectures are often distributed, ephemeral, and dynamic, making it challenging to track and secure digital evidence.
Containers and serverless functions can be short-lived and may be destroyed after execution, making traditional methods of evidence collection difficult. This can result in the loss of volatile data like logs, memory, and network traffic that would otherwise be critical to an investigation.
Elasticity: Cloud-native services scale up and down automatically, which can complicate tracking the exact time and location of an incident or attack.
Cloud-native environments are often distributed across multiple regions, availability zones, and even cloud providers. This means digital forensics teams must deal with data spread across different locations, often with varying data retention policies and access controls.
Forensic investigators need to understand inter-service communications, API calls, and cross-cloud workflows to effectively trace actions across the distributed environment.
In traditional on-premise environments, organizations have full control over their infrastructure, which simplifies evidence collection. However, in cloud-native environments, much of the underlying infrastructure (e.g., hardware, network) is managed by the cloud provider.
This raises issues around access control and chain of custody for digital evidence, as organizations may need to rely on cloud providers to gather logs or forensic data.
Microservices are often subject to changes such as scaling up or down based on demand, which creates temporary instances of services and makes it difficult to preserve evidence.
Containers and serverless functions may be instantiated dynamically and then shut down, leaving no trace of their existence unless logs or telemetry are actively captured.
A comprehensive cloud forensics framework is essential for tracking and investigating security incidents in cloud-native environments. This framework includes:
Incident Detection: Identifying a potential breach or abnormal activity using security monitoring tools like SIEM (Security Information and Event Management) and IDS/IPS (Intrusion Detection/Prevention Systems).
Data Collection: Collecting logs, metadata, and artifacts from containers, cloud orchestration platforms (e.g., Kubernetes), and serverless functions. It's critical to set up log aggregation systems from the beginning.
Chain of Custody: Ensuring that all digital evidence is properly handled, stored, and protected during the investigation, ensuring its integrity for legal or compliance purposes.
In cloud-native environments, forensic evidence can be found in several sources:
Cloud provider logs: These can include access logs, network traffic logs, and resource usage data. Cloud providers like AWS, Azure, and Google Cloud offer various logging and monitoring services (e.g., AWS CloudTrail, Azure Monitor, Google Cloud Logging).
Container Logs: Container logs (e.g., from Docker or Kubernetes) can provide detailed insights into the activities of services within containers, including errors, requests, and system events.
Network Traffic: Capturing and analyzing network traffic between microservices or to/from the internet can reveal malicious activity or unauthorized access attempts.
Cloud Storage: Cloud-native applications often rely on cloud storage solutions (e.g., AWS S3, Azure Blob Storage), and these can hold valuable evidence such as compromised data or malicious payloads.
Cloud-based Security Tools: Leveraging security tools within the cloud environment (e.g., AWS GuardDuty, Azure Security Center, Google Cloud Security Command Center) can help detect and respond to incidents early.
Kubernetes Forensics: Tools like KubeAudit or Kube-hunter can help assess vulnerabilities in Kubernetes clusters and track security incidents within the orchestration layer.
Container Forensics: Investigating container environments can be done using tools like Containerd and Sysdig to monitor the container lifecycle and retrieve logs or memory dumps.
Cloud Provider Tools: Many cloud providers offer native tools to assist in forensics. For example, AWS CloudTrail for logging API requests, AWS GuardDuty for threat detection, or Azure Sentinel for advanced threat hunting.
Immutable Infrastructure: Design infrastructure that minimizes changes and supports rapid deployment and rollback, making it easier to track incidents and preserve evidence.
Logging and Monitoring: Enable comprehensive logging and monitoring across all components of the environment (e.g., microservices, containers, serverless functions). Use centralized log aggregation platforms to collect data for future forensics.
Version Control: Use version control for code, configurations, and infrastructure definitions to track changes that might relate to an incident.
Network Segmentation: Use network segmentation to minimize the blast radius of a potential attack. If one service is compromised, it will be harder for attackers to move laterally across the environment.
Access Management: Employ least-privilege access controls and strong authentication mechanisms (e.g., MFA). Use services like AWS IAM or Azure AD to enforce access policies.
Data Encryption: Ensure that all sensitive data is encrypted both in transit and at rest to prevent exposure during a forensic investigation.
Pre-Incident Preparation: Build forensic capabilities into the cloud-native infrastructure, such as setting up log aggregation systems (e.g., AWS CloudWatch, Google Cloud Logging) from the outset.
Automation: Automate forensic data collection and monitoring using cloud-native tools and Serverless functions to capture logs and artifacts continuously.
Third-Party Security Tools: Integrate third-party tools like CloudPassage or Qualys for vulnerability scanning and forensic investigations across containerized and cloud environments.
Cloud providers may store data in different countries, which raises data sovereignty issues. Digital forensic teams must understand where the data resides and ensure compliance with relevant laws (e.g., GDPR, HIPAA).
Ensuring evidence integrity in a multi-jurisdictional environment requires understanding the chain of custody and meeting local legal requirements for data access and transfer.
Establish clear policies and procedures for handling and preserving evidence, including encryption, timestamping, and documentation of actions taken during the investigation.
Legal considerations: In cloud environments, the cloud provider may hold some evidence, which could require cooperation to access logs or storage buckets, which can be a challenge when conducting forensic investigations.
As cloud technologies evolve, so too will the tools and methodologies for cloud-native digital forensics. Emerging trends include:
AI and Machine Learning: For automating the analysis of cloud-native logs, detecting anomalies, and providing faster insights into incidents.
Cloud-native SIEMs: The development of cloud-native SIEM platforms that can ingest, analyze, and correlate data from distributed cloud environments.
Serverless Forensics: New approaches to handle forensics in serverless environments, focusing on monitoring function execution and API calls.
| Digital forensics in cloud-native environments requires innovative approaches that account for the unique challenges posed by the distributed, ephemeral nature of cloud resources. Organizations need to proactively implement forensic strategies, such as robust logging, cloud-native security practices, and understanding of the cloud infrastructure, to ensure effective response and investigation in the event of a cyber incident. |
|---|
Would you like to:
📊 Explore specific tools for cloud-native forensic investigations?
📝 Get a detailed incident response checklist for cloud environments?
🔬 Dive deeper into forensic automation using cloud-native tools?
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com