


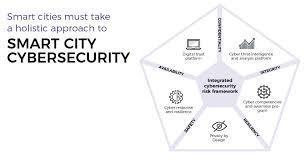
Smart cities integrate information and communication technologies (ICT) and Internet of Things (IoT) devices to:
Improve urban services (traffic, water, energy, etc.)
Enhance public safety
Optimize resources
Increase citizen engagement
They rely on real-time data collection, connectivity, automation, and AI-driven systems across critical infrastructure.
Smart cities introduce a huge attack surface with:
Billions of connected sensors and systems
Diverse stakeholders (governments, vendors, citizens)
Critical dependencies (electric grids, water supply, emergency response)
A breach doesn’t just affect data — it could mean:
Shutting down transit
Tampering with traffic signals
Disabling emergency systems
Surveillance abuse or data leaks
| Component | Cyber Risks |
|---|---|
| Smart Traffic Systems | Signal hijacking, traffic rerouting |
| Surveillance Cameras (CCTV) | Unauthorized access, facial recognition misuse |
| Public Wi-Fi Networks | Eavesdropping, man-in-the-middle (MitM) attacks |
| Energy Grids (Smart Grids) | Grid shutdowns, ransomware, data tampering |
| Water & Waste Systems | Contamination, service disruption |
| IoT Sensors & Actuators | Botnet participation, remote control by threat actors |
| Citizen Apps/Portals | Privacy breaches, data leaks, identity theft |
2016 Ukraine Power Grid Attack – Allegedly state-sponsored cyberattack led to large-scale blackout.
Atlanta Ransomware Attack (2018) – Government services offline for days; recovery cost over $17 million.
Los Angeles Smart Traffic Light Breach (ethical test) – Researchers showed traffic lights could be remotely manipulated.
Florida Water Treatment Hack (2021) – Attacker attempted to poison water supply via remote access.
Zero Trust Architecture – “Never trust, always verify”
Defense in Depth – Multiple overlapping layers of protection
Least Privilege Access – Only give access to what’s necessary
Data Minimization – Collect only the data you need
| Control | Function |
|---|---|
| Network Segmentation | Prevent lateral movement after a breach |
| IoT Security Standards | Harden devices (e.g., no default passwords) |
| Encryption of Data in Transit/At Rest | Protect sensitive data flow |
| Continuous Monitoring & Threat Detection | Detect anomalies in real time |
| Regular Patching & Firmware Updates | Close known vulnerabilities in devices |
| Identity & Access Management (IAM) | Secure logins for users, systems, devices |
NIST Cybersecurity Framework (CSF)
ISO/IEC 27001 & 27701 – Security and privacy management
ETSI EN 303 645 – Security for consumer IoT devices
IoT Security Foundation Guidelines
Smart Cities Council Cyber Resilience Guide
CISA's Infrastructure Security Guidelines
| Challenge | Description |
|---|---|
| Interoperability Issues | Diverse devices/systems from different vendors |
| Legacy Systems | Outdated infrastructure unable to support modern security |
| Privacy Concerns | Facial recognition, mass surveillance, data misuse |
| Vendor Lock-in & Trust | Can you audit and secure third-party systems? |
| AI/ML System Manipulation | Feeding fake data to influence smart decisions (e.g., traffic rerouting) |
| Physical-Cyber Integration | Physical attacks leading to cyber vulnerabilities (or vice versa) |
Blockchain for identity and secure transactions
AI for anomaly detection and threat prediction
Edge computing security for real-time analysis close to the source
Digital twins of infrastructure for simulation and security testing
Public-private cyber alliances for joint threat response
✔️ Conduct regular risk assessments
✔️ Implement SBOMs for IoT devices
✔️ Build incident response plans specific to smart systems
✔️ Train municipal staff in cyber hygiene
✔️ Engage in public transparency for citizen trust
✔️ Require secure-by-design for all tech vendors
| Smart cities can’t be smart if they’re not secure. |
|---|
| Cybersecurity must be built in from day one — not bolted on later. From smart lights to surveillance and infrastructure, resilient cities need resilient digital ecosystems. |
Would you like this tailored as:
📊 A PowerPoint presentation?
📘 A whitepaper or policy proposal?
🧱 A technical blueprint for secure smart city architecture?
Also happy to add visuals like system diagrams, threat maps, or smart city threat modeling frameworks. Just let me know!
#trending #latest

Explore the Duolingo English Test for Indian Students Abroad... Read More.

Simple Steps to Get Your Canada Student Visa in 2025... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com