

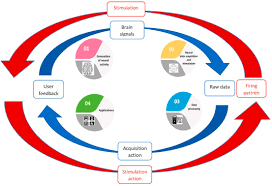
Cybersecurity for Brain-Computer Interfaces (BCIs) is an emerging and highly critical field due to the increasing integration of BCIs into various sectors like healthcare, entertainment, military, and communication. BCIs provide a direct communication pathway between the human brain and external devices, enabling new capabilities for both disabled and non-disabled individuals. However, they also introduce unique cybersecurity challenges that need to be addressed to ensure privacy, integrity, and safety.
Let’s dive into the landscape of cybersecurity for BCIs, the risks involved, and the measures necessary to secure brain-computer communication.
A Brain-Computer Interface (BCI) is a technology that facilitates direct communication between the brain and external devices, bypassing traditional output channels like the hands, voice, or eyes. BCIs can decode neural signals and translate them into commands for controlling various devices, such as:
Prosthetics and robotic limbs for medical applications.
Assistive devices for individuals with disabilities, like communication aids.
Entertainment systems that respond to mental commands (e.g., video games or virtual reality).
Military applications for enhanced cognitive control over systems.
The integration of BCIs into personal and sensitive environments creates new attack surfaces. The most significant cybersecurity risks include:
Sensitive brain data: BCIs gather highly personal and potentially sensitive neural data, such as thoughts, emotions, and intentions. If breached, this data could be used maliciously to infer private information or influence behaviors.
Unauthorized access: Hackers gaining access to the BCI system could potentially manipulate brain signals or inject misleading information into the user’s brain, creating serious privacy risks.
Malicious signal injection: A BCI could be susceptible to attacks where adversaries inject erroneous or harmful neural signals into the system, affecting user behavior or physical actions.
Hacking external devices: Hackers might gain access to the devices controlled by the BCI (e.g., robotic arms or prosthetics) and take control, causing them to behave erratically or dangerously.
Blocking communication: A DoS attack could overwhelm the communication channel between the brain and external devices, causing the system to fail or become unresponsive. This is particularly critical in medical applications where a malfunction could lead to harm or loss of control.
Mental manipulation: There is a potential for malicious actors to influence or manipulate thoughts, actions, or decisions, which raises serious ethical concerns about the abuse of BCI technology.
Legal frameworks: The lack of comprehensive legal frameworks to protect neural data and its potential misuse creates significant gaps in security and regulation.
Given the unique nature of BCIs, cybersecurity measures must be specifically designed to address these risks. Below are some critical areas for securing BCI systems:
End-to-end encryption: Just as traditional communication channels require encryption, BCI data transmissions (neural signals) must be encrypted to prevent eavesdropping or interception during transmission between the brain and external devices.
Data anonymization: Techniques should be implemented to anonymize neural data to prevent the identification of individuals from the collected data. For example, data could be stripped of personally identifiable information (PII) before being sent to storage or external devices.
User authentication: Access to the BCI system should require secure authentication methods, such as multi-factor authentication (MFA) or biometric verification, to prevent unauthorized users from gaining control over the system.
Behavioral biometrics: Continuous verification of the user can be implemented using behavioral biometrics, ensuring that the system can distinguish between the legitimate user’s neural activity and potential impersonators.
Secure communication protocols: BCIs should rely on secure communication channels for exchanging data between the device and external systems, using protocols like SSL/TLS or quantum cryptography for future-proof security.
Wireless security: As many BCIs rely on wireless communication (e.g., Bluetooth or Wi-Fi), ensuring the security of wireless communication to prevent unauthorized interception or signal manipulation is essential.
Anomaly detection: Systems should monitor for any unusual activity or anomalies in neural signals and raise alerts if unauthorized activity is detected. This could include unusual patterns of signal transmission or unexpected control of external devices.
Behavioral monitoring: Continuous monitoring of both the user’s physical actions and neural signals can help detect if an external entity is attempting to control or manipulate the system without the user’s consent.
Fail-safes for critical applications: In medical or high-stakes environments, fail-safes and redundancy mechanisms should be in place to prevent a BCI from causing harm due to a malfunction or attack. For instance, if the system detects a potential attack or failure, it could automatically disable control of sensitive devices.
Manual override: Users should always have the option for manual control of the device if the BCI system is compromised or malfunctioning.
The cybersecurity challenges specific to BCIs are still evolving, and there are several important research areas where new solutions are being developed:
Research into real-time monitoring systems and AI-powered anomaly detection is critical for identifying unauthorized interactions with BCI systems. These systems can analyze neural signals and external interactions to detect attempts to manipulate the system.
Ensuring the integrity of neural signals is crucial. Research is being done to design tamper-proof devices that make it difficult for attackers to modify neural signals without detection.
Blockchain technology can be utilized for secure storage and management of brain data, ensuring tamper-proof logging and enabling users to control who has access to their data.
Decentralized BCI systems could potentially leverage blockchain for transparent and secure management of neural data, giving users more control over their data and minimizing the risk of unauthorized access.
AI and machine learning algorithms can be used to analyze the huge amounts of data generated by BCIs in real-time, detecting unusual patterns that could indicate malicious activity or system malfunction.
Ethical hacking and penetration testing of BCI systems will be essential to identify vulnerabilities before malicious actors can exploit them. Researchers in ethical hacking can simulate attacks on BCIs to uncover potential weaknesses in the system's design or implementation.
As the development of BCIs progresses, there is a growing need for international standards and regulations to govern their security and ethical use. Some key considerations include:
GDPR (General Data Protection Regulation) and similar data protection regulations will play a crucial role in safeguarding neural data. Organizations must comply with laws related to the collection, processing, and storage of personal brain data.
HIPAA (Health Insurance Portability and Accountability Act) in the U.S. could apply in medical BCI applications, requiring healthcare providers and manufacturers to ensure the confidentiality and integrity of BCI-related health data.
Developing international standards for the secure use of BCIs, such as ISO/IEC 27001 (information security management systems), could help establish a common framework for designing secure systems and ensuring interoperability between different BCI devices.
Ethical guidelines should be established to prevent the manipulation of brain activity for malicious purposes. Research into neuroethics will be crucial in establishing ethical boundaries in BCI technology, especially in the realms of mental manipulation, consent, and autonomy.
The integration of BCIs into mainstream applications will continue to evolve, and so too will the cybersecurity measures needed to protect them. Key developments to look forward to include:
Advanced encryption methods: Quantum cryptography could provide next-generation encryption to secure neural data transmission.
Integrated security solutions: BCIs will likely come with built-in security features that seamlessly integrate with other systems, such as secure authentication and real-time threat detection.
User-driven data control: The ability for users to have complete control over who accesses their neural data, with clear transparency on how their data is used.
| As Brain-Computer Interface (BCI) technology continues to evolve and integrate into diverse sectors, cybersecurity becomes crucial to safeguard users' mental privacy, prevent unauthorized control, and ensure the safety of external devices. |
|---|
| BCI cybersecurity must evolve alongside technological advances. Addressing the vulnerabilities inherent in this groundbreaking technology will require a multi-disciplinary approach, combining expertise in neural engineering, cybersecurity, law, and ethics. |
Would you like to:
🔐 Explore specific security tools for BCIs?
📊 Learn about emerging regulations in BCI cybersecurity?
🧑💻 Understand the technical components of securing BCI systems?
#trending #latest

Simple Steps to Get Your Canada Student Visa in 2025... Read More.

Australia's Election May Cut International Students, Raise Visa Fees... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google's Ironwood chip boosts AI processing and app speed
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com